Attack Surface Management - An Essential Element of Cyber Hygiene
What is Attack Surface Management?
Attack Surface Management (ASM) is a cybersecurity discipline that involves identifying, cataloguing, and managing the externally visible and exploitable areas of an organization's digital presence.
The attack surface of an organization includes any point where unauthorized users or malicious actors can interact with systems, find vulnerabilities, and potentially gain access. These points of interaction can range from digital aspects such as network ports, webpages, and email servers, to human elements like employees susceptible to phishing attacks.
The aim of ASM is to systematically reduce the attack surface by uncovering, securing, and continuously monitoring these potential points of exploitation. This proactive approach helps prevent breaches by limiting the opportunities that attackers have to infiltrate the organization's systems and data.
ASM is a critical part of a comprehensive cybersecurity strategy, complementing other aspects such as Vulnerability Management, Threat Intelligence, and Incident Response. By reducing and securing the attack surface, organizations can significantly enhance their overall security posture and resilience against cyber threats.
Relating ASM to Vulnerability Management
Before we delve deeper into ASM, it's useful to note how ASM relates to Vulnerability Management (VM). VM is a set of processes to find and remediate only flaws in code and configuration wherever those flaws may exist, be they on internet-connected endpoints (e.g. laptops and phones) or routers and switches isolated from the internet and deep inside the network. On the other hand, ASM considers all types of flaws beyond those existing in code and configurations, but is limited in scope to only the assets that are accessible to the internet.
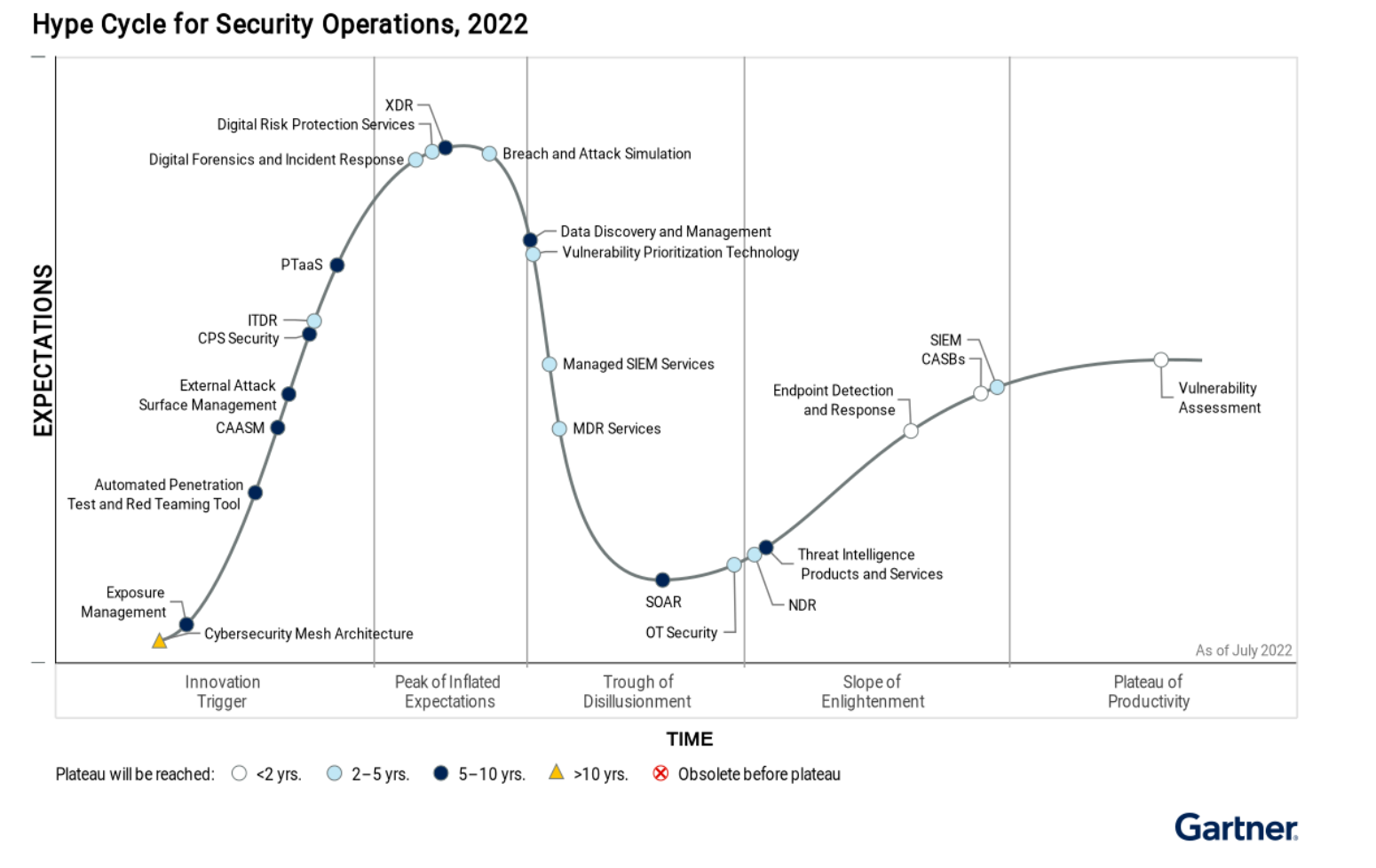
From an industry perspective, you might see ASM referred to as External Attack Surface Management (EASM), which Gartner placed in the "innovation trigger" zone according to its 2022 Hype Cycle infographic. That means that we can expect ASM/EASM to stay a hot topic in the minds of cybersecurity professionals for at least a little while (i.e. until it peaks and then troughs). For a good comparison of ASM/EASM with a yet newer tool called Continuous Asset and Attack Surface Management (CAASM), check out this article. CAASM is interesting because it answers the question "if you can detect and track all cyber hygiene issues for external assets, why not do it for internal assets as well?" (Spoiler alert: it's harder to catalogue and track internal assets and their cyber hygiene issues.)
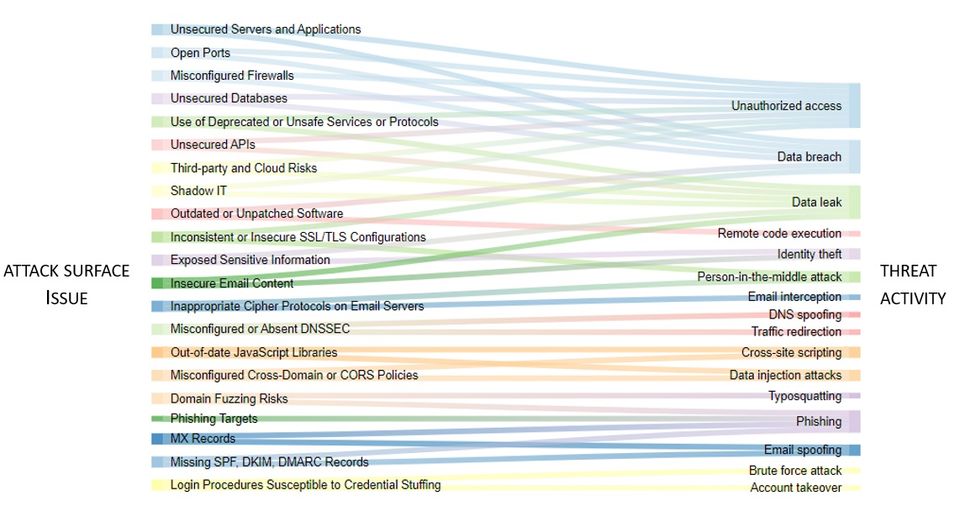
Key Areas of Attack Surface Management
In an effort to gain a better sense of ASM, we can itemize and organise the list of common cyber hygiene issues typically addressed by ASM.
1. Network and Infrastructure Security
- Unsecured and Unpatched Servers and Applications
- Open Ports
- Misconfigured Firewalls
- Inconsistent or Insecure SSL/TLS Configurations
- Use of Deprecated or Unsafe Services or Protocols
- Misconfigured or Absent DNSSEC
2. Web and Application Security
- Outdated or Unpatched Software
- Unsecured APIs
- Out-of-date JavaScript Libraries
- Misconfigured Cross-Domain or CORS Policies
- Domain Fuzzing Risks
3. Data and Information Security
- Exposed Sensitive Information
- Unsecured Databases
- Login Procedures Susceptible to Credential Stuffing
4. Third-Party and Cloud Security
- Third-party and Cloud Risks
- Shadow IT
5. Email and Communication Security
- MX Records
- Inappropriate Cipher Protocols on Email Servers
- Missing SPF, DKIM, DMARC Records
- Insecure Email Content
6. Social Engineering and Phishing Targets
- Phishing Targets
Details, Infographic and Chart
In the infographic below, we can see the relationships between the ASM issues and specific types of cyber threat activity.
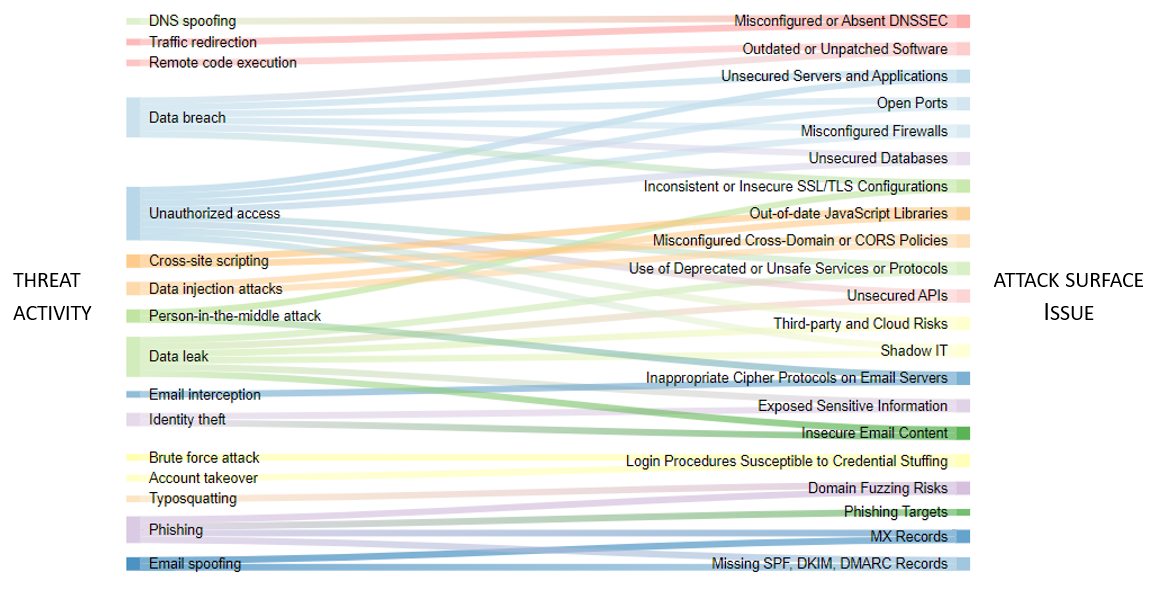
The table below delves into details about ASM issues, examples, and detection methods from ASM tools, as well as the relevant threat activity.
Hygiene Domain | ASM Issue | Issue Description | Issue Example | Related Threat Activity | ASM Detection Method |
Network and Infrastructure Security | Unsecured or unpatched Servers and Applications | Servers and applications that haven't been patched or configured properly | A web server running an outdated Apache version | Unauthorized access, data breach | Checks for updates and patches on servers and applications |
Network and Infrastructure Security | Open Ports | Network ports that are open and accessible, potentially presenting a security risk | A database port accessible from the internet | Unauthorized access, data breach | Scans for open ports across network |
Network and Infrastructure Security | Misconfigured Firewalls | Firewalls that haven't been configured properly to secure the network | Inbound traffic permitted from all sources | Unauthorized access, data breach | Reviews firewall rules and configurations |
Network and Infrastructure Security | Inconsistent or Insecure SSL/TLS Configurations | Inconsistent or outdated SSL/TLS configurations | Web server using deprecated SSLv3 | Man-in-the-middle attack, data breach | Checks SSL/TLS versions and configurations |
Network and Infrastructure Security | Use of Deprecated or Unsafe Services or Protocols | Usage of old or unsafe network services or protocols | FTP service in use for file transfer | Data leak, unauthorized access | Scans for use of deprecated or unsafe services or protocols |
Network and Infrastructure Security | Misconfigured or Absent DNSSEC | DNS records without the necessary security configurations | DNS records without DNSKEY or DS record. | DNS spoofing, traffic redirection | Checks DNS records for presence and correct configuration of DNSSEC |
Web and Application Security | Outdated or Unpatched Software | Software applications that haven't been updated or patched, leading to potential vulnerabilities | Outdated WordPress version used in production | Remote code execution, data breach | Checks versions of all software and compares with latest versions |
Web and Application Security | Out-of-date JavaScript Libraries | Usage of old or vulnerable JavaScript libraries | Website using old version of jQuery susceptible to XSS | Cross-site scripting, data injection attacks | Checks versions of JavaScript libraries used by websites |
Web and Application Security | Unsecured APIs | APIs that haven't been secured, potentially leading to data leaks or unauthorized access | API endpoint leaking user data | Data leak, unauthorized access | Checks API endpoints for potential data leaks |
Web and Application Security | Misconfigured Cross-Domain or CORS Policies | Improper configuration of Cross-Origin Resource Sharing (CORS) or cross-domain policies | Wildcard (*) in place of source restriction in CORS policy | Cross-site scripting, data injection attacks | Checks web server configurations for proper CORS and cross-domain policies |
Web and Application Security | Domain Fuzzing Risks | Risks associated with domain fuzzing, like the creation of similar-looking domain names | Registration of domain "goggle.com" as a misspelling of "google.com" | Typosquatting, phishing attacks | Performs domain fuzzing to identify potential risky domain permutations |
Data and Information Security | Exposed Sensitive Information | Sensitive information that has been exposed, potentially leading to data leaks | Unencrypted customer data accessible over the internet | Data leak, identity theft | Scans web pages and databases for potential data leaks |
Data and Information Security | Unsecured Databases | Databases that haven't been secured, potentially leading to unauthorized access | MongoDB database accessible without password | Unauthorized access, data breach | Checks for unprotected databases and their configurations |
Data and Information Security | Login Procedures Susceptible to Credential Stuffing | Websites that don't have protections against credential stuffing attacks | Website allows unlimited login attempts | Brute force attack, account takeover | Checks websites for login limit and Captcha implementation |
Third-Party and Cloud Security | Third-party and Cloud Risks | Risks associated with using third-party services or cloud platforms | Data stored unencrypted on third-party storage service | Data leak, unauthorized access | Evaluates third-party services for data storage and transfer |
Third-Party and Cloud Security | Shadow IT | Usage of unauthorized software or devices within an organization | Unofficial use of personal Dropbox account for work documents | Data leak, unauthorized access | Scans network for unapproved software and devices |
Email and Communication Security | MX Records | MX records that have been misconfigured, potentially leading to email spoofing or phishing attacks | MX records incorrectly configured | Email spoofing, phishing attacks | Checks configuration of MX records in DNS |
Email and Communication Security | Inappropriate Cipher Protocols on Email Servers | Email servers using weak or deprecated cipher suites | Email server using weak or deprecated cpher like TLS 1.1 and SSL 3.0 | Man-in-the-middle attack, email interception | Checks email server configurations for cipher suite |
Email and Communication Security | Missing SPF, DKIM, DMARC Records | Email domains that don't have SPF, DKIM, and DMARC records, potentially leading to email spoofing or phishing attacks | Domain lacks necessary email validation records | Email spoofing, phishing attacks | Checks DNS for SPF, DKIM, DMARC records |
Email and Communication Security | Insecure Email Content | Emails that contain sensitive data in plaintext, potentially leading to data leaks | Email content includes sensitive data in plaintext | Data leak, identity theft | Scans emails for sensitive data |
Social Engineering and Phishing Targets | Phishing Targets | Potential targets for phishing or spear-phishing attacks | Employee email addresses available on the company website | Phishing, spear-phishing attacks | Identifies potential information that could be used for phishing |
By identifying, cataloguing, and monitoring points of potential exploitation in an organization's digital presence, ASM plays a vital role in minimizing the opportunities cyber threat actors have to infiltrate and wreak havoc. With industry leaders like Gartner acknowledging its innovative prowess, we can anticipate ASM to be important elements in cybersecurity strategies for the foreseeable future.