What is the Cyber Second Line of Defense?
Understanding the Three Lines of Defense Model
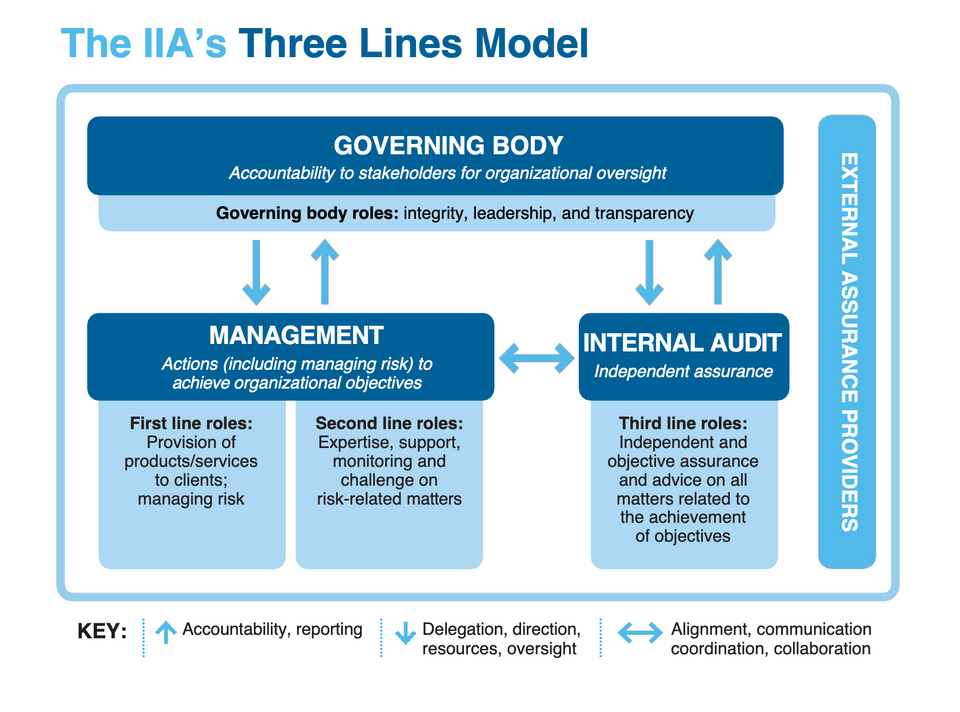
The Three Lines of Defense model is a widely accepted framework used in risk management (originally created in the early 2000's by the Institute of Interal Auditors -IIA). In the world of cybersecurity, the concept of layered defense is not new. It's a strategy that has been borrowed from military tactics and applied to the digital realm with great success. The Three Lines of Defense model has been appropriated by the cybersecurity community and used as a guide by enterprise and organizations of any larger size to structure their cybersecurity programs and improve their outcomes.
It's important to note that when referring to layers in cybersecurity we often think of layering technical controls like multifactor-authentication (MFA), segmentation, and encryption. The Three Lines of Defense Model is a risk-control approach insofar as it is geared towards helping organizations identify who is responsible for managing risk, and ensures that there are multiple checks and balances in place.
Here's how it breaks down:
First Line of Defense - Operational Management: This includes the cybersecurity and IT units and functions that own and manage operations and infrastructure. They are responsible for implementing security controls and procedures. These are your cybersecurity professionals detecting threats, patching systems, pentesting, handling incidents and more.
Second Line of Defense - Risk Management and Compliance Oversight: This line of defense provides oversight and ensures the first line is effectively managing the risks. They develop the risk management framework and strategy, and ensure compliance with it. They often participate in incident management and collaborate closely with the First Line to ensure that thebest practices are implemented, gaps are identified and addressed, and that the organization's cybersecurity posture is improving over time
Third Line of Defense - Internal Audit: This is an independent group that provides assurance to the organization's board of directors and senior management on the effectiveness of governance, risk management, and internal controls.
This site is dedicated to understanding the ideas, best practices and challenges related to the Cyber Second Line of Defense.