How to Do a Cyber Risk Assessment (Part 2 - Threat Description)

In Part 1, we introduced the concept of risk assessment. Now, we delve deeper into the risk assessment process, beginning with the first step: Threat Description. (Jump here to get to the example).
The strategic to tactical funnel
Threat description requires a comprehensive examination of the cyber threats your organization could face. The idea is to rule out threat activity that your organisation is unlikely to fact, and concentrate on the threat activity that you are likely to face. You need to ask the questions:
- What are the common types of cyberattacks out there?
- Which of these are likely to target organizations like yours?
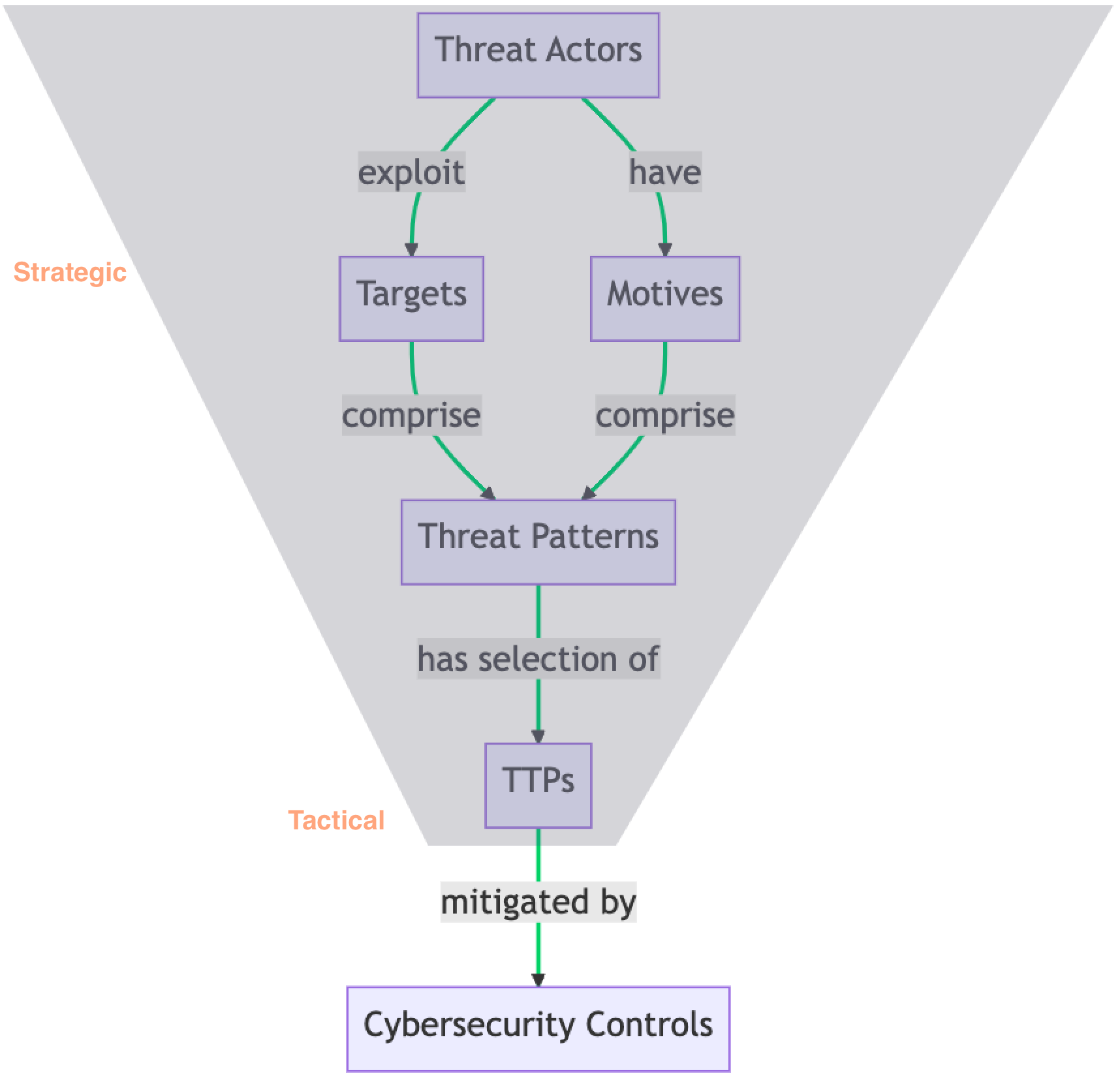
The answer to these questions is best developed by starting with the strategic 10,000 ft view. You want to use your strategic understanding to focus downward and develop a tactical understanding. In other words, you want to understand who the threat actors are, what they generally target and why, the ways in which they undertake their threat activity (also known as a threat pattern) and the Tactics, Techniques and Procedures (TTPs). inherent in those threat patterns. Once you can drill down to the appropriate TTPs, you are where you want to be! You will be able to invest in the cybersecurity controls that best block those TTPs. In this way, your investments are targeted at the risk that you face, and not just a theoretical and general cybersecurity risk landscape. Check out Figure 1 below for a representation of the funnel.
Figure 1: The Strategic to Tactical Funnel
Getting trustworthy information
High-level trends at the strategic level don't tend to change from week or week, month to month, or sometimes even year to year. For example, ransomware and business email compromise have been plaguing commercial enterprise for years. As you drill down, however, you will see that the operational activities of the threat actors - and certainly their tactics - are constantly evolving, as the cat and mouse dynamic of threat action versus security control continues on.
For that strategic, 10,000 ft view, the good news is that there is enough in the public domain to put together a very good picture. To make sense of the strategic threat landscape, it's important to understand the fundamental categories of threat activity. These include the types of threat actors, types of victims (categorized by geographical location, type of organization, financial resources, etc.), and their motivations.
While strategic-level information remains more or less constant over a considerable period, TTPs are far more dynamic and subject to rapid changes. There are several reasons for this.
- Threat actors continually adapt their TTPs in response to improvements in defensive security measures. Every time a new patch or security update is released, for example, attackers have to modify their strategies to circumvent these defenses. This cycle creates a continually evolving landscape of cyber threats.
- As cyber threat intelligence improves, so too does our understanding of the TTPs employed by threat actors. With each new discovery or incident response, we gain new insights into their methods and behavior. This leads to regular updates in our understanding and categorization of TTPs.
- Changes in technology, such as the advent of cloud computing, IoT, AI, and other advances, can significantly impact TTPs. Threat actors often exploit the vulnerabilities inherent in new technologies before businesses can fully understand or mitigate them, creating an ever-changing front line in the battle of cybersecurity.
Happily, a vast amount of information about TTPs is readily available in the public domain. Various cybersecurity forums, blogs, publications, and threat intelligence platforms publish new findings on a daily basis. This dissemination of information has the potential to foster a collaborative environment in the cybersecurity community and improve overall defensive postures.
Most importantly, there are a set of robust frameworks that allow you to make sense of the strategic to tactical funnel. These frameworks have been created by experts and non-profit organizations such as the National Institute of Standards and Technology (NIST), MITRE, and the Center for Internet Security (CIS). They provide a structured approach that allows for the mapping of threat patterns to TTPs to cybersecurity controls.
There is enough high quality in the public domain to go from strategic, to threat patterns to TTPs. And from there to the cybersecurity safeguards. That said, you need to know what sources to trust and how to interpret them.
Trusted Sources From Strategic to Tactical
When putting together the threat landscape, it's very important to consult a broad range of sources and compare the data and findings among them. Every organization, whether its mission is public or private, national or multi-national, will have a specific lens through which it views the cyber threat landscape. This perspective will inevitably shape the info they gather and the assessments the produce.
If you feel you are thin on subject matter expertise, one approach you can take is that when you observe consensus among a variety of high quality sources and their data seem to mutually reinforce one another, there's a high probability that the information is reliable. Nonetheless, always maintain a critical eye, considering the underlying motivations and biases that may influence these assessments. Knowing the trusted sources is essential to this approach. You've got to avoid getting your information from random, unverifiable, uninformed or heavily biased sources!
Sources - Strategic landscape and threat patterns
To develop a strategic understanding of the threat landscape and the threat patterns, you should consult publicly-released cyber threat assessments from reputable federal cybersecurity organizations. These include the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the Canadian Centre for Cyber Securit, the UK National Cyber Security Centre, and the Australian Cyber Security Centre.
In addition to these organizations, there are a number of respected bloggers with valuable insights on cybersecurity and cyber threats. Notable figures include Brian Krebs and Bruce Schneier. Institutions dedicated to cybersecurity knowledge and training, like the SANS Institute and the Cyentia Institute, also provide a wealth of knowledge.
When it comes to vendors, they can be another fantastic source of information. However, it's important to distinguish between vendors who operate on the internet with broad access to cyber threat data, and those in the cybersecurity industry whose primary business model is oriented towards cybersecurity.
For vendors in the latter category, they might possess a narrower or specific view of threats, due to the focus of their business activities. Hence, caution should be exercised when evaluating their assessments. Examples of these include CrowdStrike, Sophos, Cisco, Mandiant, Trendmicro.
Vendors like Microsoft and Verizon have an exceptionally wide view of internet activity, thanks to their extensive deployments on computers or coverage of Internet pipes or both. Given the prevalence, for example, of Microsoft Defender across countless endpoints, these vendors are in a unique position to provide detailed and accurate annual reports on the state of cyber threats.
Sources - TTPs
The above sources will provide you with excellent understanding of the strategic landscape as well as threat patterns. Now that you know what kinds of threat patterns are most relevant to your organisation, you can investigate the relevant TTPs. A great place to get that information is the Cybersecurity & Infrastructure Security Agency (CISA), as well as threat blogs and websites such as SANS and the InfoSec Institute. The content on these platforms comes from high-quality sources and cybersecurity experts, providing timely updates on newly discovered threats, vulnerabilities, and exploits. They often delve into the specifics of different TTPs, and that helps you stay informed about the latest developments
Open-source threat databases such as the VERIS Community database (VCDB) offer another layer of intelligence. The VCDB provides a wealth of cybersecurity incident data, freely accessible for analysis. It can be an invaluable resource for professionals seeking to understand the current threat landscape and analyze trends over time. However, to effectively harness the potential of such resources, it's important to possess or develop data science skills. With these skills, you can manipulate and analyze the data, creating actionable insights that can help inform your security strategy.
Once you've got a sense of the relevant TTP's, you can use frameworks such as the ATT&CK database maintained by the Mitre corporation. It stands as a global knowledge base of cyber threat TTPs based on real-world observations. The ATT&CK matrix categorizes and describes all the various known ways that threat actors can exploit systems. Mitre has also created a Mitigations database, which map cybersecurity controls to the TTPs described in the ATT&CK matrix.
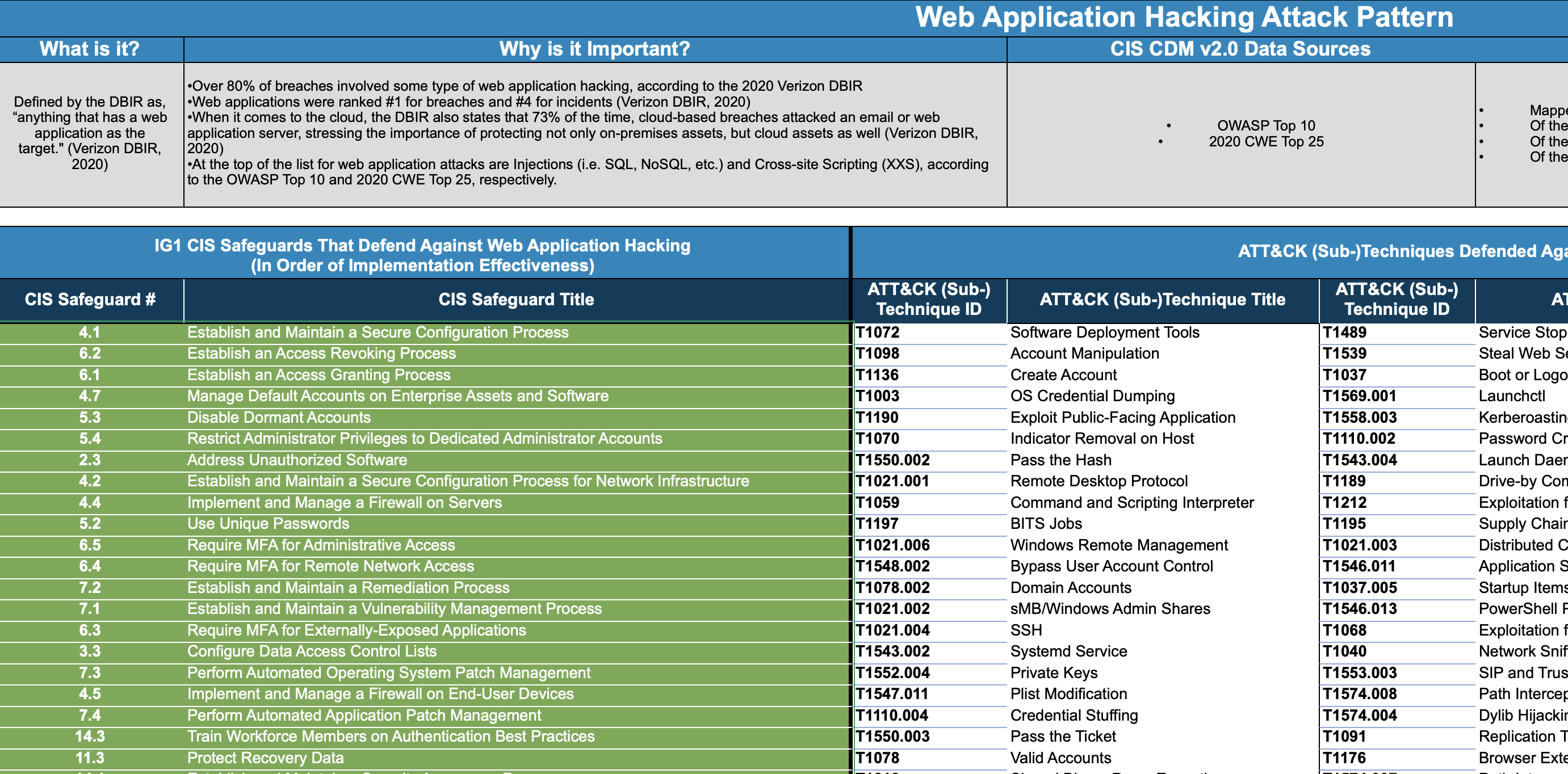
There are other reputable organisations that have similarly useful frameworks such as the Center for Internet Security (CIS). CIS produces more user-friendly documents that tend to boil things down, which is very useful for small and medium enterprise and those who crave something more accessible than extremely detailed frameworks. The CIS Community Defense Model 2.0, does an amazing job of moving us down the strategic to tactical funnel: in it they analyse the Mitre ATT&CK framework, identifying threat patterns along the way (e.g. ransomware, web application hacking, etc.) and map it to their CIS Controls. They've made the Community Defense Model available free of charge (just need to create an account to access the free download), and the xls version of the analysis is available as their "CIS Attack Card".
Example of how to put the threat picture together
CASE STUDY: Risk to a Small Business (5 employees) in the professional services (consulting) sector
Let's begin with selecting our most trusted sources of information. In this case, we'll use the following three anchor documents:
- 2023-2024 National Cyber Threat Assessment issued by the Canadian Centre for Cyber Security
- 2022 Verizon Data Breach Investigations Report
- 2022 Cyentia Information Risk Insights Study

These documents provide a comprehensive overview of the current threat landscape, detailing the various categories of threat actors - from nation-states to cybercriminals - and their motivations, be it geopolitical, financial, or otherwise.
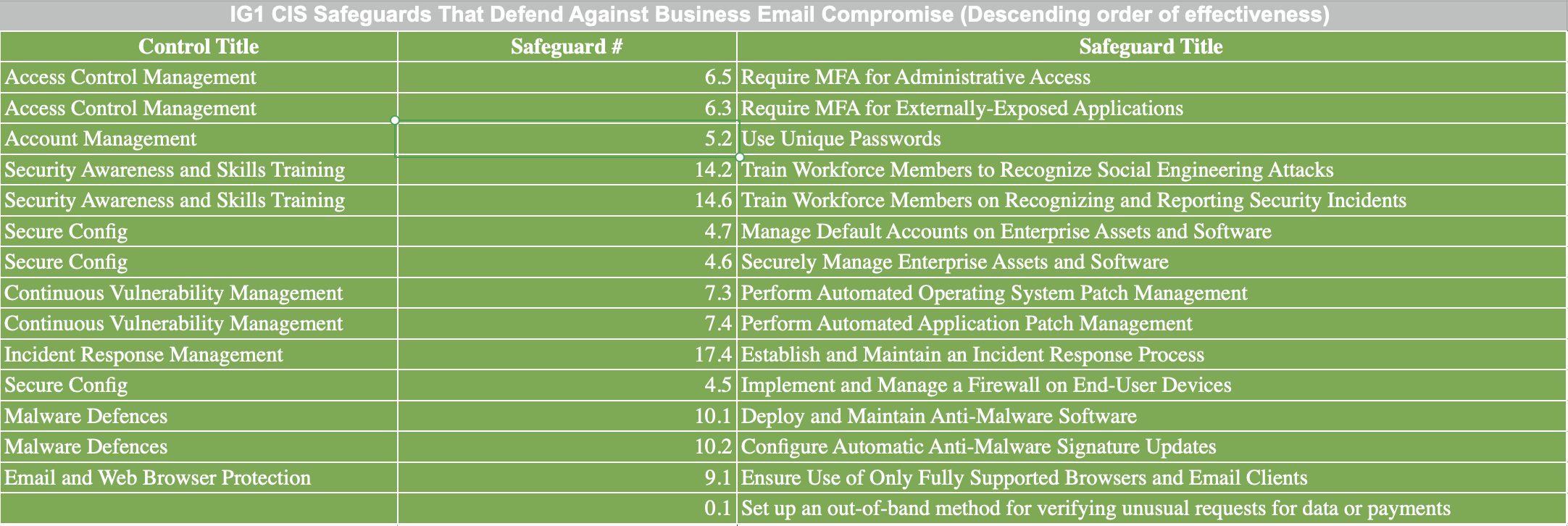
From the Verizon DBIR, we learn that for small businesses, ransomware and business email compromise (BEC) are the primary concerns. This is crucial information for our small consulting firm - it allows us to focus our efforts on the threats that are most relevant to us.
The Cyentia study reinforces this focus. According to their data, ransomware, "scam or fraud", and targeted intrusion are the most impactful types of events relative to their frequency. We can rule out targeted intrusion, but "scam or fraud" includes BEC, and we've already identified ransomware as a key concern. This alignment between the DBIR and Cyentia study gives us confidence in our focus areas: ransomare and BEC
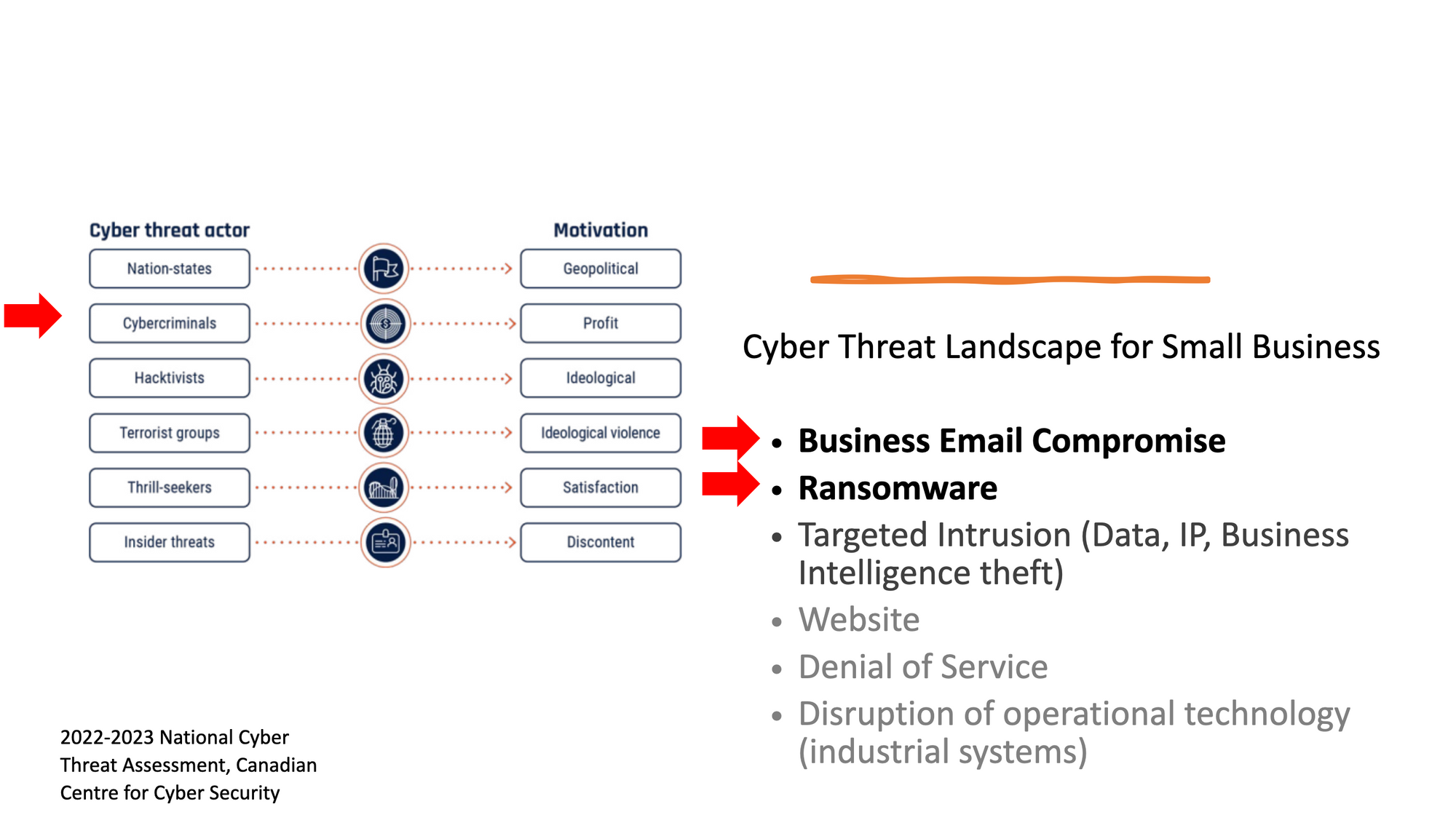
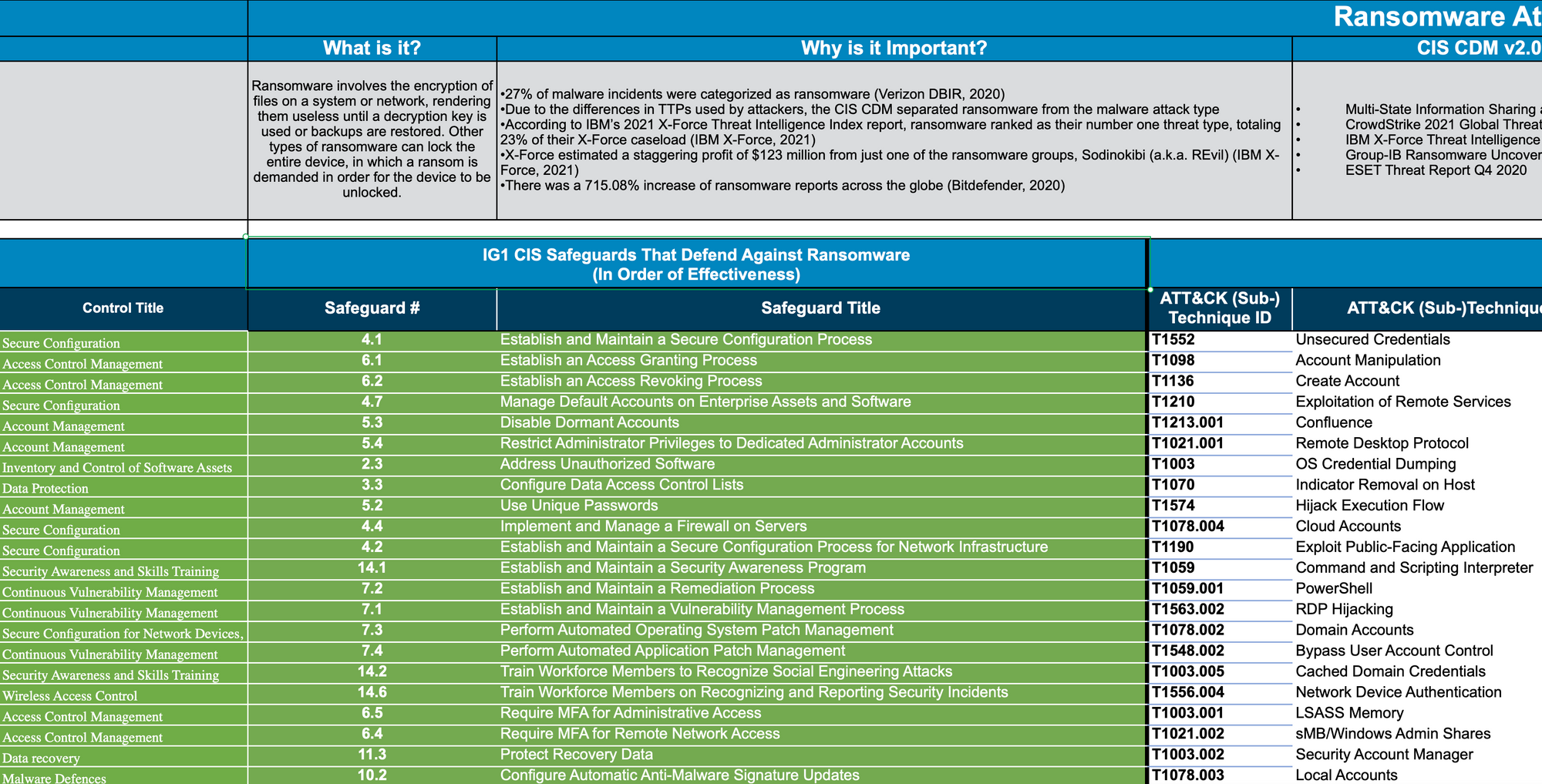
With this understanding of the threat landscape, we can now identify the relevant Tactics, Techniques, and Procedures (TTPs) associated with these threats. The Center for Internet Security (CIS) provides "attack cards" that identify ransomware as an attack pattern, including associated TTPs and controls. They don't have one for BEC, but I've created one below, which maps relevant TTPs and controls.
This process gives us a clear picture of the attack patterns relevant to our business, the associated TTPs, and the controls that can mitigate these threats. We are now ready for the next step in our cybersecurity journey: assessing the expected impact of these threats.