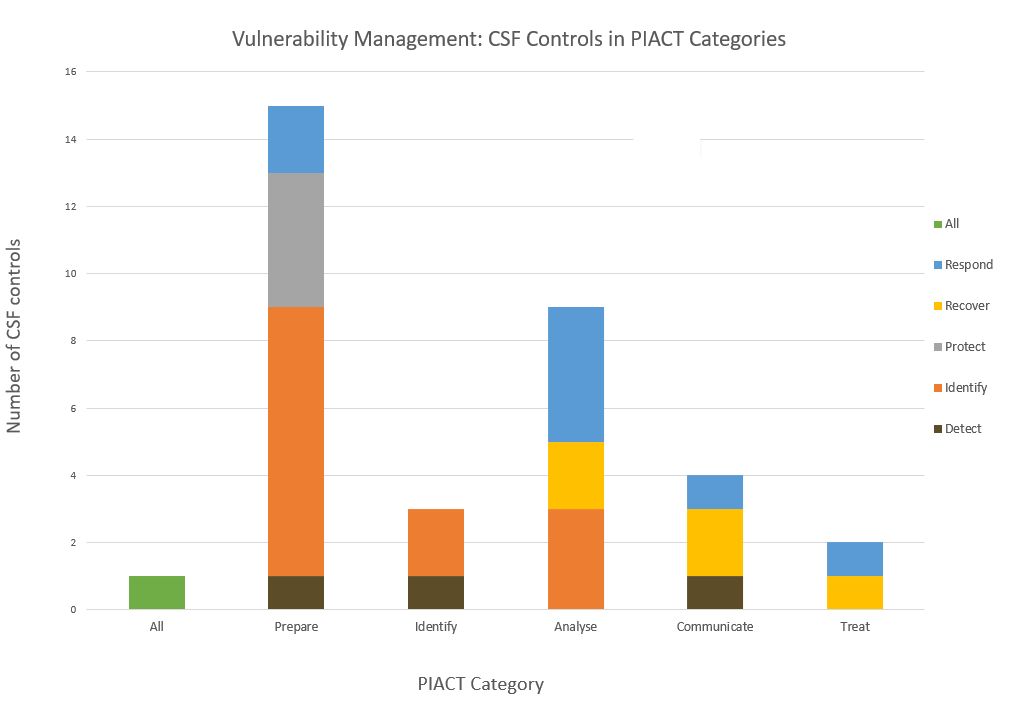
Enhancing Vulnerability Management with Frameworks (Part 1): NIST CSF and a Modified SANS PIACT
Part 1 (mapping PIACT to NIST CSF)
The NIST Cybersecurity Framework (CSF) is a highly respected guide for managing and reducing cybersecurity risk. However, when it comes to vulnerability management, its structure may not be the most intuitive. The SANS PIACT (Prepare, Identify, Assess, Communicate, Treat) framework aligns more closely with the lifecycle of vulnerability management. We can use PIACT to pull out the relevant CSF controls, which then opens open a whole world of possibilities because that gets us into an ecosystem of a dozen different frameworks that have already been mapped to one another.
But great as the PIACT conception is, I think it could be even better with some slight modifications. Of my changes, the most important one is ensuring that the intake of intelligence/vendor information about vulnerabilities is clearly defined as a sub-category in the "Identify" category. Here's a summary of the changes:
- Prepare: No change
- Identify: Change the sub-categories to (1) Scanning (i.e. network scanning and host based agents), (2) Intelligence/information (i.e. from vendors), and (3) CVD (i.e. coordinated vulnerability disclosure policies and pathways that allow security researchers to ethically disclosure vulnerabilities that they have discovered). These sub-categories better reflect the full suite of activities required in the "Identify" category.
- Analyze: No change
- Communicate: add a sub-category called Compliance. This addition reflects the fact that some of the CSF controls are squarely aimed at compliance as a separate activity from other forms of metrics and reporting.
- Treat: No change
Using PIACT to identify NIST CSF controls
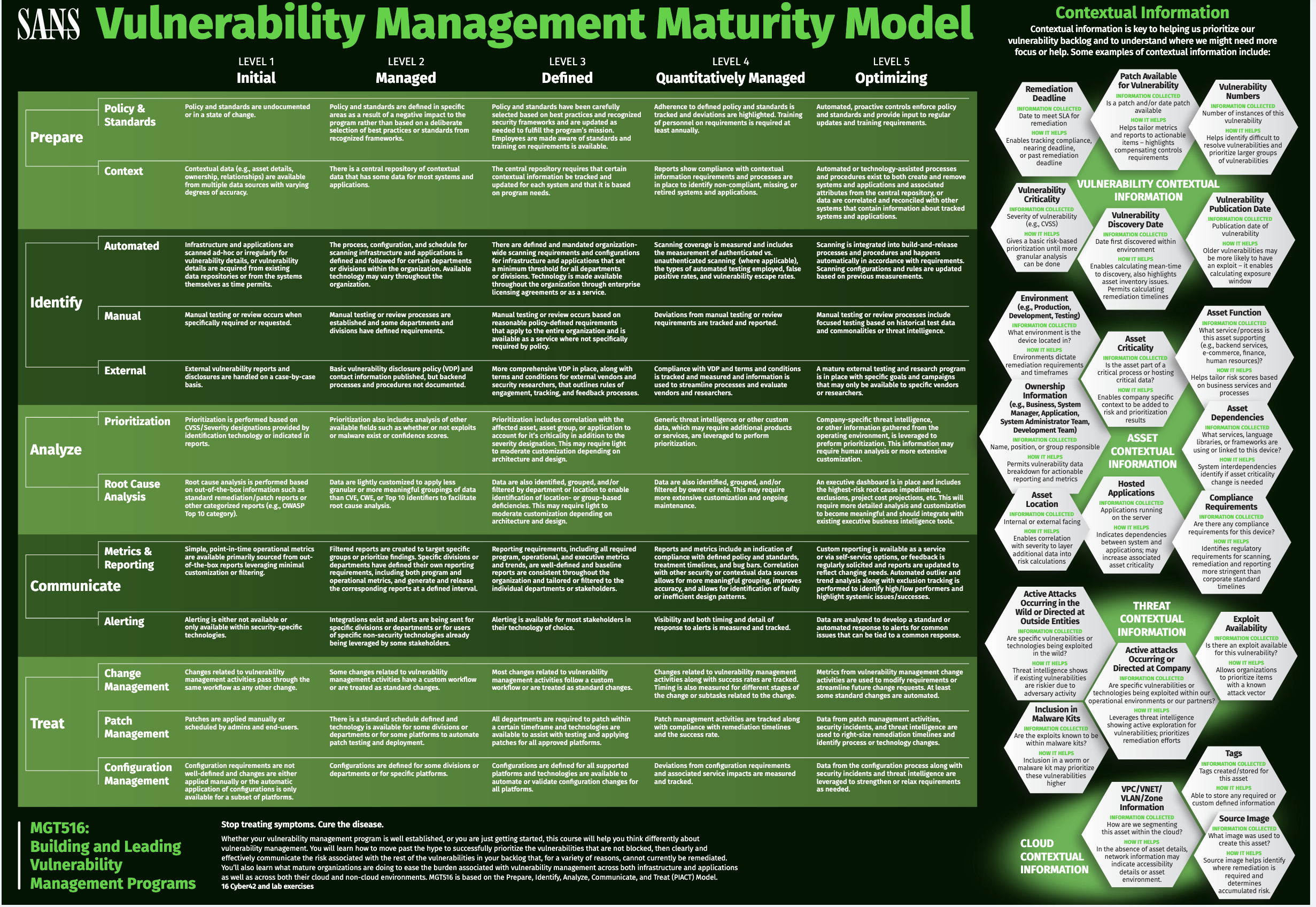
Moving from PIACT to NIST CSF is important because of the ecosystem of frameworks that are already mapped to the NIST CSF. I went through each of the 108 NIST CSF controls in v1.1 (published in 2018) and identified 34 that pertain to vulnerability management, and map back to PIACT. You will find the mapping in the diagram below.
There are a few items worth noting. Firstly, there is a CSF sub-control (PR.IP-12: A vulnerability management plan is developed an implemented) that is a broad statement about vulnerability management. It applies to all aspects of the PIACT cycle so I've included it in every PIACT category.
Secondly, the CSF main categories of Identify, Protect, Detect, Respond, Recover has a sequencing logic to ie (i.e. you identify and protect things first and when things go wrong you detect them, respond and then recover) that aligns decently with PIACT, which also has a sequencing logic to it. However, in PIACT, there are some activities in the "Treat" category that will precede some aspects of the "Communication" category. For instance, doing the work (i.e. patching) will occur before compliance metrics and reports are created.
Lastly, a couple of CSF controls marked as Respond in CSF are categorized as "Prepare" in PIACT, and that results in a disparity in sequencing (i.e. items at the end of the CSF sequence are at the beginning of the PIACT sequence). But if you take a look at the wording of these two CSF controls, I think they reflect things you'd like to have accomplished earlier rather than later.
- RS.CO-1: Personnel know their roles and order of operations when a response is needed.
- RS.AN-5: Processes are established to receive, analyze, and respond to vulnerabilities disclosed to the organization from internal and external sources (e.g., internal testing, security bulletins, or security researchers).
Here's a look at the SANS PIACT framework after my modifications, and mapped to the corresponding CSF controls:
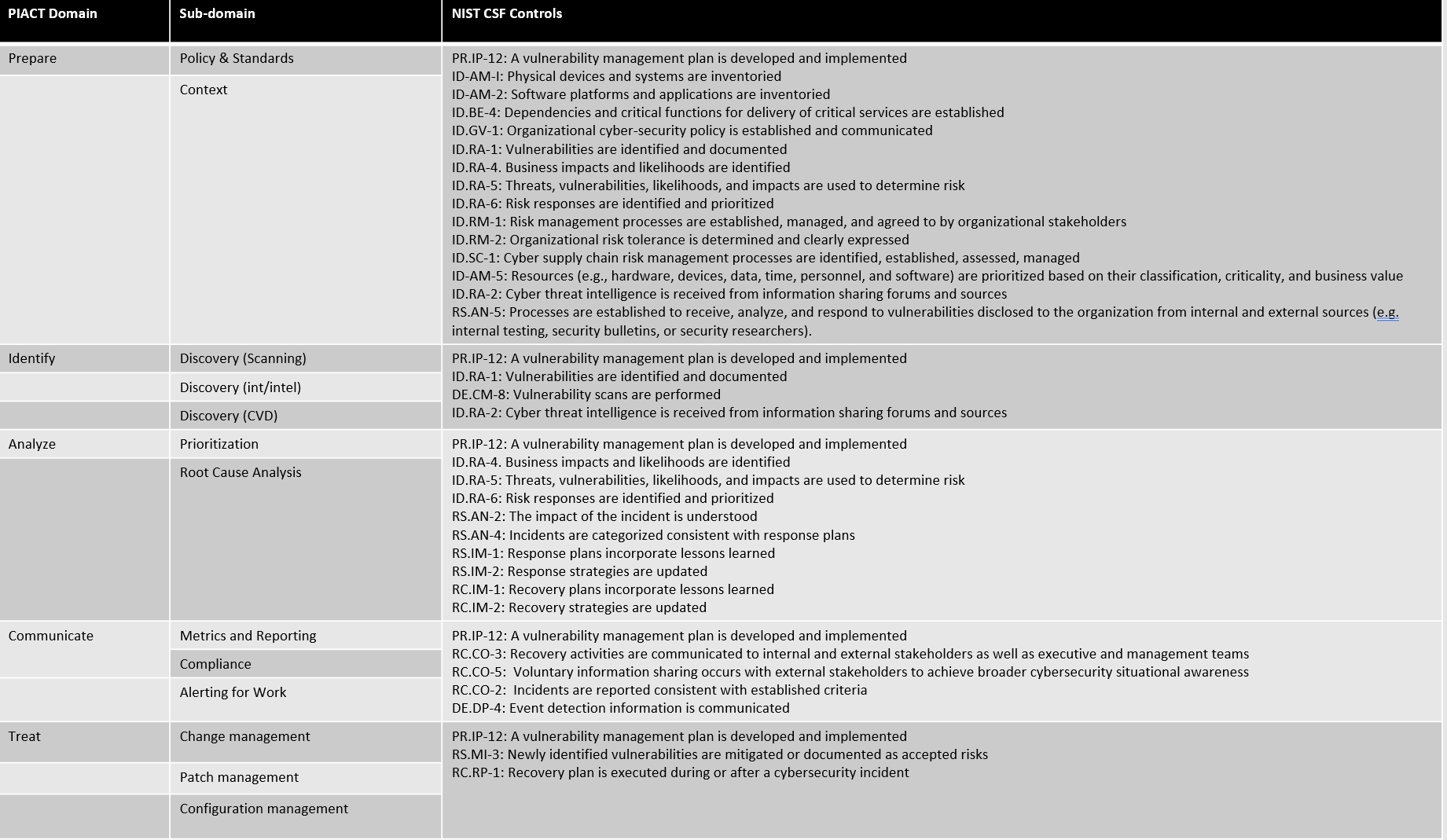
Here's a graphical summary of the information: