Vulnerability Management

Elevating Your Vulnerability Management Program: A Practical Guide
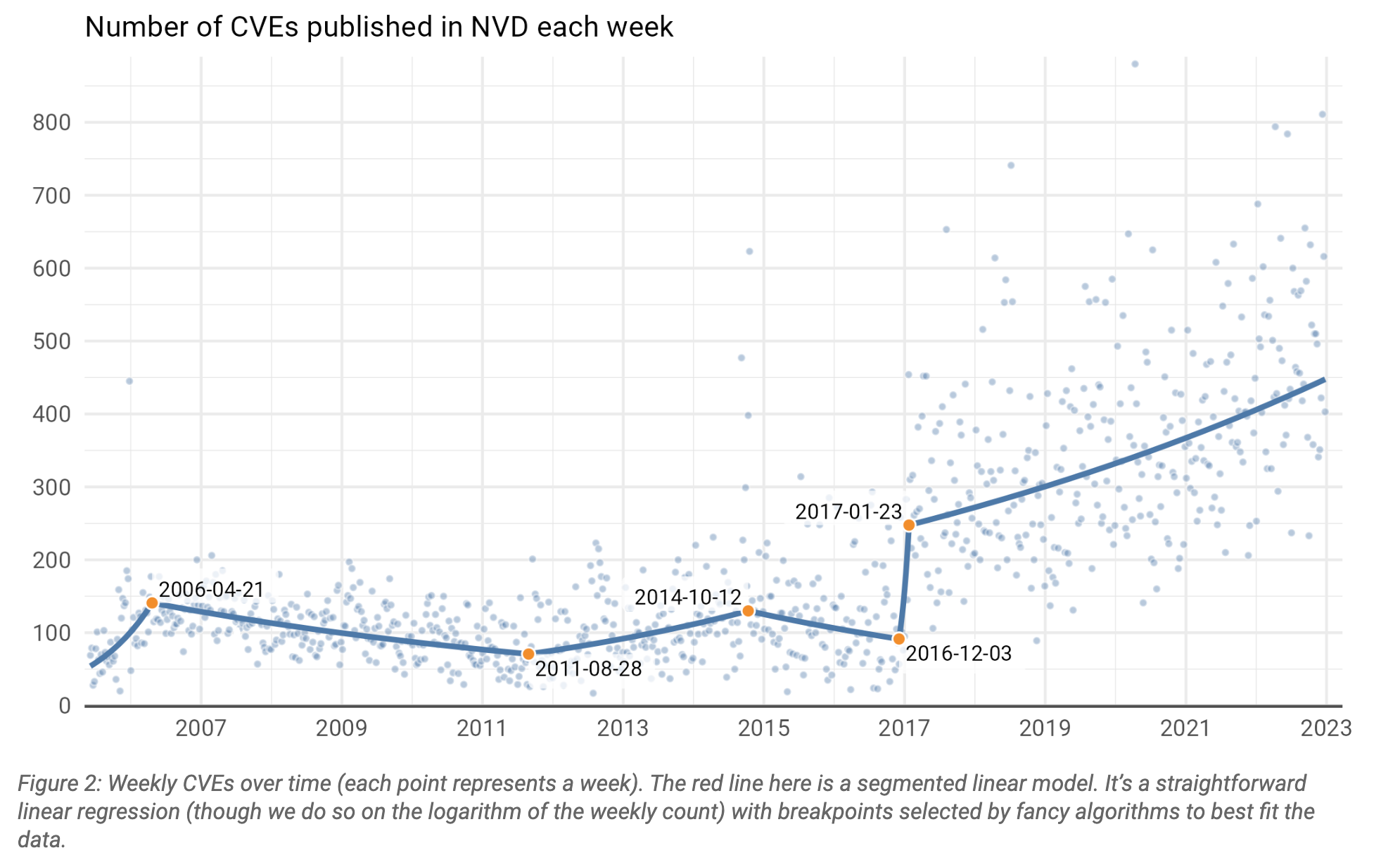
In the realm of cybersecurity, some topics naturally command the spotlight. They're the headline-grabbers, the subjects of heated debates and lots of commentary. Vulnerability management, however, often isn't one of those topics. It's not glamorous like AI-driven threat hunting or quantum-resistant encryption. Yet, its importance in the cybersecurity landscape is undeniable, and some of the mega incidents of 2022-2023 (e.g., Log4j, Log4shell and ProxyLogon) have only underscored this fact. What's worse is that the trend line is heading in the wrong direction, which is the result of several factors:
- The number and type of internet-connected devices continues to grow, most notably with IoT and industrial IoT.
- The mix and sourcing of software, hardware, firmware, middleware, and libraries that make up a stack continues to increases in complexity. Supply chain attacks are one manifestation of this.
- Zero-trust architecture reflects the diminishing security offered by the perimeter and the exposure of a lot of endpoints to the Internet, so vulnerabilities that were once hidden can't depend on security through obscurity anymore.
Yet, compared with other aspects of cybersecurity, with the exception of when the sh*t hits the fan, vulnerability management tends to get lost in the shuffle. But it's the diligent, behind-the-scenes efforts of finding and remediating vulnerabilities that keeps systems secure and businesses running smoothly. To complicate matters, vulnerability management relies on fundamental but often nettlesome IT capabilities such as Asset Inventory, Configuration Management, Change Management, and Patch Management.
Despite the lack of limelight, if you know where to look there are sufficient resources available to help you create and mature your vulnerability management program. Here are the three buckets of extremely useful resources, and I've included many more below.
- How to do vulnerability management: the NIST Guide to Enterprise Patch Management Technologies | NIST (2013). It's focussed on technologies and over ten years old at this point, but it's always useful to know what NIST has issued on a topic. For something more recent, check out the US CISA's CRR Supplemental Resource Guide, Volume 4: Vulnerability Management.
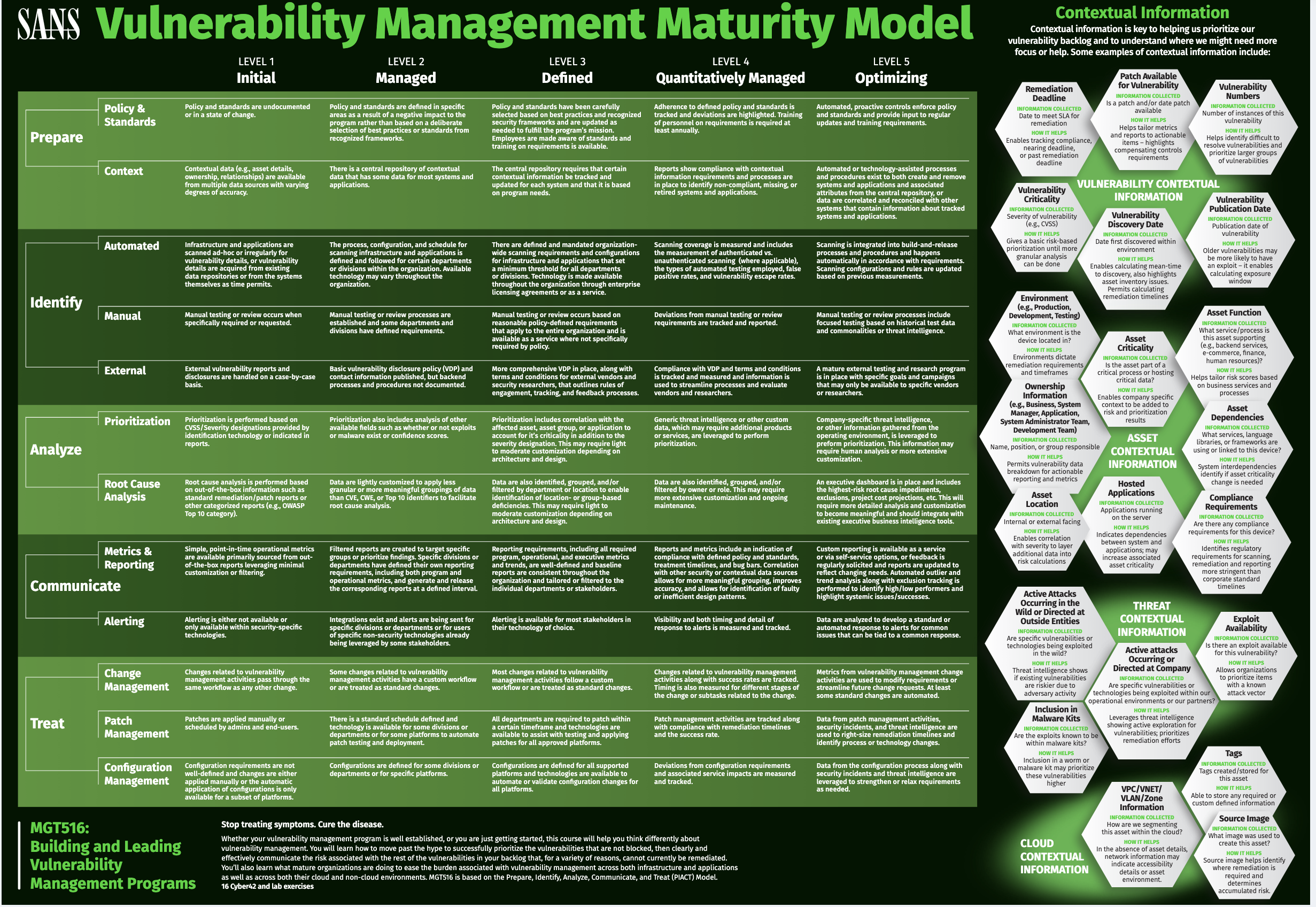
- How to measure and mature your program: The SANS vulnerability management maturity model and maturity model self-assessment tool. It gives you a general sense of the things you need to concern yourself with for effective vulnerability management: governance (policy, service level agreements, compliance metrics, and up to date asset inventory), vulnerability intelligence (from vendors, open source and coordinated vulnerability disclosure), vulnerability awareness (internal scanning and agents), vulnerability risk assessments (severity and prioritisation of vulnerabilities), remediation (doing the work to update and path, and linking in wit CMDB, change management and patch management).
- Examples of vulnerability management policies: The State of Massachusetts published a vulnerability management policy. And here is the Government of Ontario enterprise vulnerability management policy (Ontario is a province in Canada and has a population of about 15 million, so the provincial government IT enterprise is large.) There aren't that many governments that publish their enterprise vulnerability management policies, and this one has many excellent features, and gives you a sense on how a policy can address the many facets of vulnerability management in a large enterprise.
Additional Resources
Podcasts


SANS course

Guides and Tutorials:
- The Secret to Vulnerability Management - Video by SANS Instructor David Hazar
- CRR Supplemental Resource Guide, Volume 4: Vulnerability Management
- CDM Vulnerability Management (VUL) Capability
- Vulnerability Management Resources | SANS Institute
- Reducing the Significant Risk of Known Exploited Vulnerabilities | CISA
- Top Five Vulnerability Management Failures and Best Practices - YouTube
- https://github.com/lizfrenz/owasp-vuln-mng
Maturity Models and Guidelines:
- Vulnerability Management Maturity Model | Prism
- Essential Eight Maturity Model to ISM Mapping | Cyber.gov.au
- Essential Eight Maturity Model | Cyber.gov.au
- Vulnerability Management Maturity Model Part I | Jonathan Risto | SANS Institute
- Vulnerability Management Maturity Model Part II | Jonathan Risto | SANS Institute
- C2M2 Maturity Model
- CMMC overview maturity model
- Cybersecurity Maturity Model Certification - Model Overview
Vulnerability Management Policies
- BC Government Directory, CITZ - Vulnerability & Risk Management
- Vulnerability Management Policy : TechWeb : Boston University
- VulnerabilityManagementPolicy.pdf
- Vulnerability Management Policy | octo
- Vulnerability and Patch Management Policy | Policies and Procedures
- Vulnerability Management | Office of the VPIT-CIO | University of Michigan
- Technical Vulnerability Management policy
- Threat and Vulnerability Management control procedure | Manchester Metropolitan University
- Threat and Vulnerability Management Policy
- Vulnerability Management Policy | Office of Information Security | Washington University in St. Louis
- GO-ITS 42 Security Requirements for Enterprise Vulnerability Management | ontario.ca
- Vulnerability and Patch Management - Province of British Columbia
- Vulnerability Management Policy | EOTSS
- Enterprise Security Standards | California Department of Technology
- Vulnerability Management | Information Technology Services
- Vulnerability Management Policy
Open Source Vulnerabilities Feeds
If you have a functioning vulnerability management program, then here are free resources to keep your program up to date. If you working at a large enterprise that can splash out on vendor feeds, these will do you very well. (Hat tip to Eric at opensourcery.io, who had a very popular session entitled "Intel on a Shoestring: Building a Great Program, Even on a 3-figure Budget" at the 2023 RSAC.)
- CISA Known Exploited Vulnerabilities (KEV) Catalog https://www.cisa.gov/known-exploited-vulnerabilities-catalog
- CVE Trends https://cvetrends.com/
- Vuln Monitor https://www.vulmon.com
- Talos Vuln Report https://talosintelligence.com/vulnerability_reports
- ZDI latest posts https://www.zerodayinitiative.com/advisories/published/
- Talos 0-Day https://talosintelligence.com/vulnerability_reports#zerodays
- MITRE CVE Search https://cve.mitre.org/cve/search_cve_list.html
- NIST CVE Search https://nvd.nist.gov/vuln/search
- CVE Details DB - Search https://nvd.nist.gov/vuln/search
